How to uninstall Host Data Loss Prevention agent without using a challenge code ?
The solution has been taken from Mcafee site:
KB69151
KB69151
Problem
Unable to uninstall Host Data Loss Prevention (Host DLP) when the
Management Console has been deleted or is unavailable to provide a
challenge code.
Solution
As designed, you cannot remove the Host DLP agent without the
challenge key provided from the console unless the administrator has
disabled the uninstall challenge-response mechanism in the policy. This
is provided so that unauthorized users cannot remove the Host DLP agent
unless the administrator explicitly configures the policy to allow it.
To configure the policy to allow unchallenged uninstalls:
To configure the policy to allow unchallenged uninstalls:
- Log on to the ePO 4.x console.
- Click Menu, Data Protection, DLP Policy.
- Set the Show Challenge-Response on uninstall option to Disable under the Advanced Configuration tab in the policy.
Workaround
Uninstall the agent through an ePO task on the affected computers:
- Log on to the ePO 4.5 console.
- Click System Tree.
- Create a new subgroup:
- Click System Tree Actions, New Subgroup.
- Type a name for the group, and click OK.
- Select the affected computers.
- Click Actions, Directory Management, Move Systems.
- Select the newly created group and click OK.
- Create a new client task:
- Click the Client Tasks tab.
- Click New Task under Actions.
- In the Name field, type a name for the task. (for example, Remove DLP Agent.)
- In the Type field, select Product Deployment, and click Next.
- In the Products and Components field, select Data Loss Prevention 9.0.0.
- In the Action field, select Uninstall, and click Next.
- Click Next.
- Change the Schedule Type to Run immediately, and click Next.
NOTE: The task is scheduled for the next time the McAfee Agent updates the policy. To force the installation to take place immediately, send an agent wake-up call.
- After the task has completed, restart the affected computers.
McAfee Host Data Loss Prevention Missing "RUN CLIENT TASK" option in Server Task
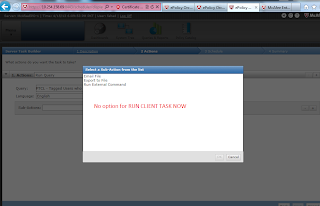
When we create a New Query for DLP and try to create a server task to lets suppose deploy DLP Agents on systems that have particular tag, for that we need to have the following:
1. Create a Query to filter machines with specific tag
2. Create Server task and select the query created in the first step
3. In Sub-Action select RUN CLIENT TASK NOW option to deploy DLP agents.
While we observer that only 3 options were showing instead of many options that should have been present.
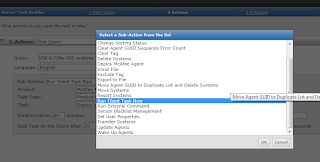
But we have figured out that the option was missing as shown in the
first figure, we did alott of testing multiple creating queries
and thanks to Mark from Mcafee DLP we were able to find out the cause.
SOLUTION
The RUN CLIENT TASK NOW options and many other options will only and only show when while creating the Queries, we select the Chart Type as "TABLE"
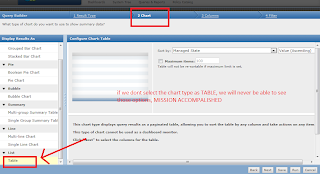
we selected this option for the chart type and were able to see RUN CLIENT TASK NOW option.
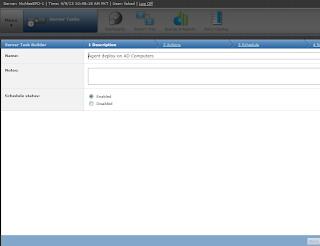
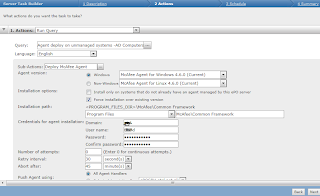
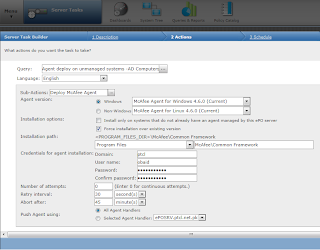
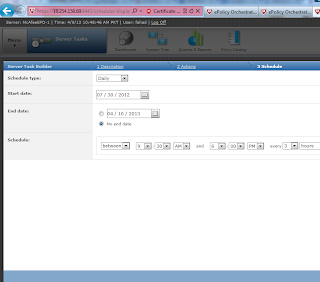
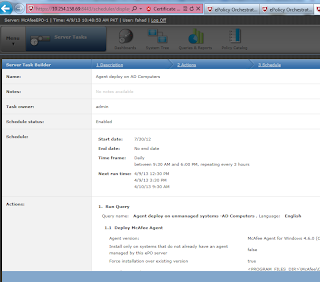
How to auto Deploy Mcafee ePO 4.6 agents on Windows machines ?
In order to auto Deploy Mcafee ePO 4.6 agents on Windows machines we
need to develop a Server task. Please follow the screenshots to have a
view.








Ports needed by ePO 4.x and ePO 5.0 for communication through a firewall
Environment:
McAfee Agent 4.x
McAfee ePolicy Orchestrator 5.0
McAfee ePolicy Orchestrator 4.x
McAfee ePolicy Orchestrator 5.0
McAfee ePolicy Orchestrator 4.x
Summary:
The following tables display the ports needed by ePolicy Orchestrator (ePO) for communication through a firewall:For the purpose of this article:
- Bi-directional means that a connection can be initiated from either direction
- Inbound means the connection is initiated by a remote system
- Outbound means the connection can be initiated by the local system
ePO 4.5:
| Port | Default | Description | Traffic direction |
| Agent to server communication port | 80 | TCP port opened by the ePO Server service to receive requests from agents. The repository is also hosted on this port. | Bi-directional between the Agent Handler and the ePO server and inbound to the Agent Handler from the McAfee Agent. |
| Agent communicating over SSL (4.5 and later agents only) | 443 | By default, 4.5 agents should communicate over SSL (443 by default). | Inbound connection to the Agent Handler from the McAfee Agent. |
| Agent wake-up communication port SuperAgent repository port |
8081 | TCP port opened by agents to receive agent wakeup requests from the ePO server. TCP port opened to replicate repository content to a SuperAgent repository. |
Outbound connection from the ePO server/Agent Handler to the McAfee Agent. |
| Agent broadcast communication port | 8082 | UDP port opened by SuperAgents to forward messages from the ePO server/Agent Handler. | Outbound connection from the SuperAgents to other McAfee Agents. |
| Console-to-application server communication port | 8443 | HTTPS port opened by the ePO Application Server service to allow web browser UI access. | Inbound connection to the ePO server from ePO Console. |
| Client-to-server authenticated communication port | 8444 | HTTPS port opened by the ePO Application Server service to receive RSD connections. Also, used by the Agent Handler to talk to the ePO server to get required information (like LDAP servers). | Inbound connection to the ePO server from the Rogue System Sensor. Outbound connection from remote Agent Handlers to the ePO server. |
| Security threats communication port | 8801 | HTTP port hosted by McAfee Labs for retrieving security threat feed. Note that this port cannot be changed. | Outbound connection from the ePO server the external McAfee Labs server. |
| SQL server TCP port | 1433 | TCP port used to communicate with the SQL server. This port is specified or determined automatically during the setup process. | Outbound connection from the ePO server/Agent Handler to the SQL server. |
| SQL server UDP port | 1434 | UDP port used to request the TCP port that the SQL instance hosting the ePO database is using. | Outbound connection from the ePO server/Agent Handler to the SQL server. |
| Default LDAP server port | 389 | LDAP connection to look up computers, users, groups, and Organizational Units for User Based Policies. | Outbound connection from the ePO server/Agent Handler to an LDAP server. |
| Default SSL LDAP server port | 636 | User Based Policies use the LDAP connection to look up users, groups, and Organizational Units. | Outbound connection from the ePO server/Agent Handler to an LDAP server. |
ePO 4.6 and 5.0:
| Port | Default | Description | Traffic direction |
| Agent to server communication port | 80 | TCP port opened by the ePO Server service to receive requests from agents. | Bi-directional between the Agent Handler and the ePO server and inbound to the Agent Handler from the McAfee Agent. |
| Agent communicating over SSL (4.5 and later agents only) Software Manager |
443 | By default, 4.5 agents should communicate over SSL (443 by default). This port is also used for the remote Agent Handler to communicate with the ePO Master Repository. | Inbound connection to the Agent Handler from the McAfee Agent. |
| Agent wake-up communication port SuperAgent repository port |
8081 | TCP port opened by agents to receive agent wakeup requests from the ePO server. TCP port opened to replicate repository content to a SuperAgent repository. |
Outbound connection from the ePO server/Agent Handler to the McAfee Agent. |
| Agent broadcast communication port | 8082 | UDP port opened by SuperAgents to forward messages from the ePO server/Agent Handler. | Outbound connection from the SuperAgents to other McAfee Agents. |
| Console-to-application server communication port | 8443 | HTTPS port opened by the ePO Application Server service to allow web browser UI access. | Inbound connection to the ePO server from ePO Console. |
| Client-to-server authenticated communication port | 8444 | HTTPS port opened by the ePO Application Server service to receive RSD connections. Also, used by the Agent Handler to talk to the ePO server to get required information (like LDAP servers). | Inbound connection to the ePO server from the Rogue System Sensor. Outbound connection from remote Agent Handlers to the ePO server. |
| Security threats communication port | 8801 | HTTP port hosted by McAfee Labs for retrieving security threat feed. Note that this port cannot be changed. | Outbound connection from the ePO server the external McAfee Labs server. |
| SQL server TCP port | 1433 | TCP port used to communicate with the SQL server. This port is specified or determined automatically during the setup process. | Outbound connection from the ePO server/Agent Handler to the SQL server. |
| SQL server UDP port | 1434 | UDP port used to request the TCP port that the SQL instance hosting the ePO database is using. | Outbound connection from the ePO server/Agent Handler to the SQL server. |
| Default LDAP server port | 389 | LDAP connection to look up computers, users, groups, and Organizational Units for User Based Policies. | Outbound connection from the ePO server/Agent Handler to an LDAP server. |
| Default SSL LDAP server port | 636 | User Based Policies use the LDAP connection to look up users, groups, and Organizational Units. | Outbound connection from the ePO server/Agent Handler to an LDAP server. |
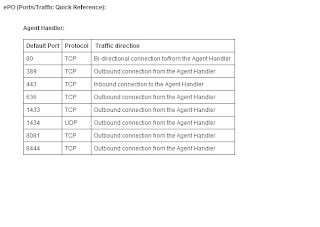
ePO (Ports/Traffic Quick Reference):
Agent Handler:
Default Port Protocol Traffic direction 80 TCP Bi-directional connection to/from the Agent Handler 389 TCP Outbound connection from the Agent Handler 443 TCP Inbound connection to the Agent Handler 636 TCP Outbound connection from the Agent Handler 1433 TCP Outbound connection from the Agent Handler 1434 UDP Outbound connection from the Agent Handler 8081 TCP Outbound connection from the Agent Handler 8444 TCP Outbound connection from the Agent Handler
ePO Server:
Default Port Protocol Traffic direction 80 TCP Bi-directional connection to/from the ePO server 389 TCP Outbound connection from the ePO server 443 TCP Inbound/Outbound connection to/from the ePO server 636 TCP Outbound connection from the ePO server 1433 TCP Outbound connection from the ePO server 1434 UDP Outbound connection from the ePO server 8081 TCP Outbound connection from the ePO server 8443 TCP Inbound connection to the ePO server 8444 TCP Inbound connection to the ePO server 8801 TCP Outbound connection from the ePO server
McAfee Agent:
Default Port Protocol Traffic direction 80 TCP Outbound connection to the ePO server/Agent Handler 443 TCP Outbound connection to the ePO server/Agent Handler 8081 TCP Inbound connection from the ePO server/Agent Handler. If the agent is a SuperAgent repository then inbound connection from other McAfee Agents. 8082 UDP Inbound connection to Agents. Inbound/Outbound connection from/to SuperAgents
SQL Server:
Default Port Protocol Traffic direction 1433 TCP Inbound connection from the ePO server/Agent Handler 1434 UDP Inbound connection from the ePO server/Agent Handler
How To Setup McAfee Agent Handler ?
Please see the following SNAP SHOT. Agent
Handler can only be installed on Windows Server 2003 SP 2 / Windows
Server 2008 in Windows environment.
Agent Handler SETUP can be found in McAfee ePO setup.
Double click on this Agent Handler folder and Execute the Setup file
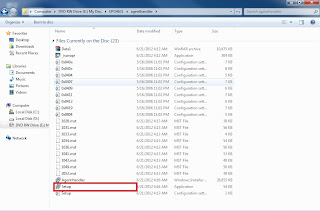
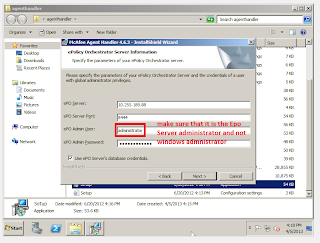
Setup will ask for details of your ePO sever and its administrator password.
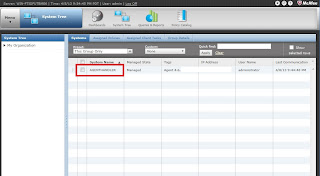
After Installation is completed, Agent Handler will be visible in your ePO Server's System Tree Automatically.
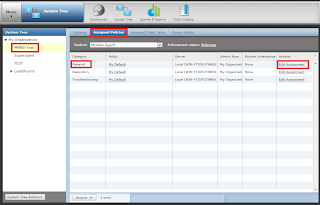
Make a new Sub Group in System and Name it According to your need (e.g. Department name, Location etc.). this group will contain the systems that will communicate directly with the Agent Handler.
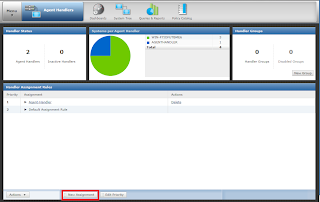
when you click new assignment tab following window will appear where you can give the details and configure your assignment rule and customize your Handler Priority.
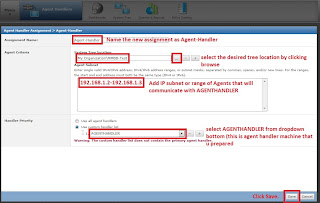
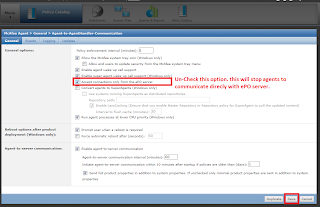
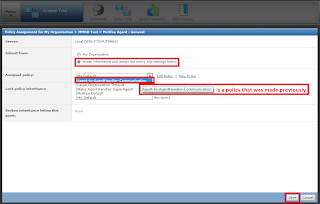
Click on Policy Catalog to create the policy that allows desired agents to communicate with Agent Handler but not with ePO server. to Create policy Duplicate the existing MY Default policy of McAfee Agent's policies and name it as you want.
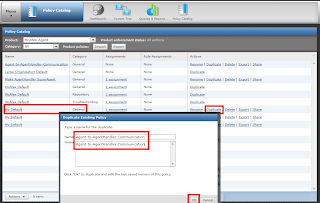
Click to edit Policy.
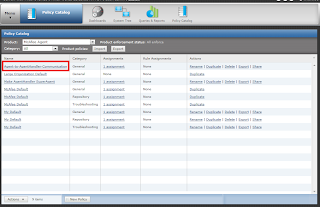
Add desired system to the Specific group on which agent handler policy needs to be applied.
do the following steps to change policy assignment. assign the policy which was created so that desired systems can communicate to agent handler to the group.
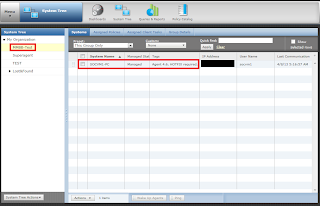
Agent Handler installation and configuration is completed. Now we have to verify that only desired systems are communicating with the agent handler. to do this we can perform following steps on host with agent.
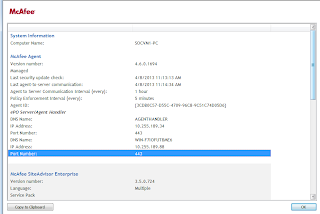
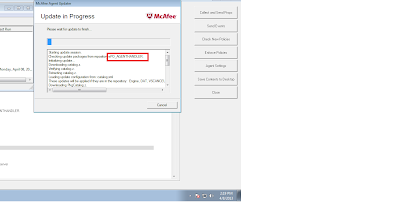
from upper SNAPSHOTS we can verify that the desired agents are communicating with the Agent Handler. to check the communication of other agents with ePO server we can perform following steps. do not get confused with the properties of McAfee agent. Run the update process to verify communication.
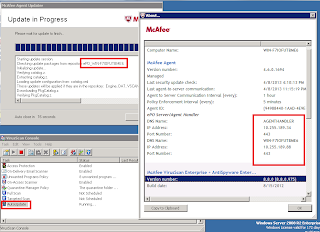
Important Ports that are needed for the Agent handler outbound and bi-directional communication.

Agent Handler SETUP can be found in McAfee ePO setup.

Double click on this Agent Handler folder and Execute the Setup file


Setup will ask for details of your ePO sever and its administrator password.


After Installation is completed, Agent Handler will be visible in your ePO Server's System Tree Automatically.

Make a new Sub Group in System and Name it According to your need (e.g. Department name, Location etc.). this group will contain the systems that will communicate directly with the Agent Handler.

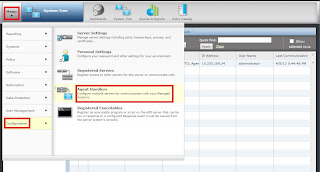
To see Agent Handler configuration , assignments and priorities please follow following SNAPSHOT.
Go to Menu, then Configuration and Click Agent Handlers.

On Agent Handler page click new assignment
to create new assignment rule so that systems that are needed to
communicate with Agent Handlers can be reached. Also this helps the
Agent Handler to service the mentioned sub-nets or clients.

when you click new assignment tab following window will appear where you can give the details and configure your assignment rule and customize your Handler Priority.

Click on Policy Catalog to create the policy that allows desired agents to communicate with Agent Handler but not with ePO server. to Create policy Duplicate the existing MY Default policy of McAfee Agent's policies and name it as you want.

Click to edit Policy.


Add desired system to the Specific group on which agent handler policy needs to be applied.

do the following steps to change policy assignment. assign the policy which was created so that desired systems can communicate to agent handler to the group.


Agent Handler installation and configuration is completed. Now we have to verify that only desired systems are communicating with the agent handler. to do this we can perform following steps on host with agent.


from upper SNAPSHOTS we can verify that the desired agents are communicating with the Agent Handler. to check the communication of other agents with ePO server we can perform following steps. do not get confused with the properties of McAfee agent. Run the update process to verify communication.

Important Ports that are needed for the Agent handler outbound and bi-directional communication.

VPN Tutorial
The Virtual Private Network - VPN - has attracted the attention of many
organizations looking to both expand their networking capabilities and
reduce their costs.
The VPN can be found in workplaces and homes, where they allow employees to safely log into company networks. Telecommuters and those who travel often find a VPN a more convenient way to stay connected to the corporate intranet. No matter your current involvement with VPNs, this is a good technology to know something about. This VPN tutorial involves many interesting aspects of network protocol design, Internet security, network service outsourcing, and technology standards.
The key feature of a VPN, however, is its ability to use public networks like the Internet rather than rely on private leased lines. VPN technologies implement restricted-access networks that utilize the same cabling and routers as a public network, and they do so without sacrificing features or basic security.
A VPN supports at least three different modes of use:
Like many commercialized network technologies, a significant amount of sales and marketing hype surrounds VPN. In reality, VPNs provide just a few specific potential advantages over more traditional forms of wide-area networking. These advantages can be significant, but they do not come for free. The potential problems with the VPN outnumber the advantages and are generally more difficult to understand. The disadvantages do not necessarily outweigh the advantages, however. From security and performance concerns, to coping with a wide range of sometimes incompatible vendor products, the decision of whether or not to use a VPN cannot be made without significant planning and preparation.
Many vendors have developed VPN hardware and/or software products. Unfortunately, immature VPN standards mean that some of these products remain incompatible with each other.
What is a VPN ?
A VPN supplies network connectivity over a possibly long physical distance. In this respect, a VPN is a form of Wide Area Network (WAN). VPNs enable file sharing, video conferencing and similar network services. Virtual private networks generally don't provide any new functionality that isn't already offered through alternative mechanisms, but a VPN implements those services more efficiently / cheaply in most cases.
A key feature of a VPN is its ability to work over both private networks as well as public networks like the Internet. Using a method called tunneling, a VPN use the same hardware infrastructure as existing Internet or intranet links. VPN technologies includes various security mechanisms to protect the virtual, private connections.
Specifically, a VPN supports at least three different modes of use:
A VPN can be set up to support remote, protected access to the corporate home offices over the Internet. An Internet VPN solution uses a client/server design works as follows:
This type of VPN use does not involve an Internet Service Provider (ISP) or public network cabling. However, it allows the security benefits of VPN to be deployed inside an organization. This approach has become especially popular as a way for businesses to protect their WiFi local networks.
The VPN can be found in workplaces and homes, where they allow employees to safely log into company networks. Telecommuters and those who travel often find a VPN a more convenient way to stay connected to the corporate intranet. No matter your current involvement with VPNs, this is a good technology to know something about. This VPN tutorial involves many interesting aspects of network protocol design, Internet security, network service outsourcing, and technology standards.
What Exactly Is A VPN?
A VPN supplies network connectivity over a possibly long physical distance. In this respect, a VPN is a form of Wide Area Network (WAN).
The key feature of a VPN, however, is its ability to use public networks like the Internet rather than rely on private leased lines. VPN technologies implement restricted-access networks that utilize the same cabling and routers as a public network, and they do so without sacrificing features or basic security.
A VPN supports at least three different modes of use:
- Remote access client connections
- LAN-to-LAN internetworking
- Controlled access within an intranet
VPN Pros and Cons
Like many commercialized network technologies, a significant amount of sales and marketing hype surrounds VPN. In reality, VPNs provide just a few specific potential advantages over more traditional forms of wide-area networking. These advantages can be significant, but they do not come for free. The potential problems with the VPN outnumber the advantages and are generally more difficult to understand. The disadvantages do not necessarily outweigh the advantages, however. From security and performance concerns, to coping with a wide range of sometimes incompatible vendor products, the decision of whether or not to use a VPN cannot be made without significant planning and preparation.
Technology Behind VPNs
Several network protocols have become popular as a result of VPN developments:
- PPTP
- L2TP
- IPsec
- SOCKS
Many vendors have developed VPN hardware and/or software products. Unfortunately, immature VPN standards mean that some of these products remain incompatible with each other.
The Future of VPN
Virtual private networks have grown in popularity as businesses to save money on remote network access for employees. Many corporations have also adopted VPNs as a security solution for private Wi-Fi wireless networks. Expect a continued gradual expansion in use of VPN technology to continue in the coming years.
What is a VPN ?
A VPN supplies network connectivity over a possibly long physical distance. In this respect, a VPN is a form of Wide Area Network (WAN). VPNs enable file sharing, video conferencing and similar network services. Virtual private networks generally don't provide any new functionality that isn't already offered through alternative mechanisms, but a VPN implements those services more efficiently / cheaply in most cases.
A key feature of a VPN is its ability to work over both private networks as well as public networks like the Internet. Using a method called tunneling, a VPN use the same hardware infrastructure as existing Internet or intranet links. VPN technologies includes various security mechanisms to protect the virtual, private connections.
Specifically, a VPN supports at least three different modes of use:
- Internet remote access client connections
- LAN-to-LAN internetworking
- Controlled access within an intranet
Internet VPNs for Remote Access:
In recent years, many organizations have increased the mobility of their workers by allowing more employees to telecommute. Employees also continue to travel and face a growing need to stay connected to their company networks.
A VPN can be set up to support remote, protected access to the corporate home offices over the Internet. An Internet VPN solution uses a client/server design works as follows:
-
1. A remote host (client) wanting to log into the company network first connects to any public Internet Service Provider (ISP).
2. Next, the host initiates a VPN connection to the company VPN server. This connection is made via a VPN client installed on the remote host.
3. Once the connection has been established, the remote client can communicate with the internal company systems over the Internet just as if it were a local host.
VPNs for Internetworking:
Besides using virtual private networks for remote access, a VPN can also bridge two networks together. In this mode of operation, an entire remote network (rather than just a single remote client) can join to a different company network to form an extended intranet. This solution uses a VPN server to VPN server connection.
Intranet / Local Network VPNs:
Internal networks may also utilize VPN technology to implement controlled access to individual subnets within a private network. In this mode of operation, VPN clients connect to a VPN server that acts as the network gateway.
This type of VPN use does not involve an Internet Service Provider (ISP) or public network cabling. However, it allows the security benefits of VPN to be deployed inside an organization. This approach has become especially popular as a way for businesses to protect their WiFi local networks.
Switch (Network Switch)
A network switch is a small hardware device that joins multiple computers together within one local area network (LAN). Technically, network switches operate at layer two (Data Link Layer) of the OSI model.
Network switches appear nearly identical to network hubs, but a switch generally contains more intelligence (and a slightly higher price tag) than a hub. Unlike hubs, network switches are capable of inspecting data packets as they are received, determining the source and destination device of each packet, and forwarding them appropriately. By delivering messages only to the connected device intended, a network switch conserves network bandwidth and offers generally better performance than a hub.
As with hubs, Ethernet implementations of network switches are the most common. Mainstream Ethernet network switches support either 10/100 Mbps Fast Ethernet or Gigabit Ethernet (10/100/1000) standards.
Different models of network switches support differing numbers of connected devices. Most consumer-grade network switches provide either four or eight connections for Ethernet devices. Switches can be connected to each other, a so-called daisy chaining method to add progressively larger number of devices to a LAN.
Network switches appear nearly identical to network hubs, but a switch generally contains more intelligence (and a slightly higher price tag) than a hub. Unlike hubs, network switches are capable of inspecting data packets as they are received, determining the source and destination device of each packet, and forwarding them appropriately. By delivering messages only to the connected device intended, a network switch conserves network bandwidth and offers generally better performance than a hub.
As with hubs, Ethernet implementations of network switches are the most common. Mainstream Ethernet network switches support either 10/100 Mbps Fast Ethernet or Gigabit Ethernet (10/100/1000) standards.
Different models of network switches support differing numbers of connected devices. Most consumer-grade network switches provide either four or eight connections for Ethernet devices. Switches can be connected to each other, a so-called daisy chaining method to add progressively larger number of devices to a LAN.
Routing
In internetworking, the process of moving a packet of data from source to destination. Routing is usually performed by a dedicated device called a router. Routing is a key feature of the Internet
because it enables messages to pass from one computer to another and
eventually reach the target machine. Each intermediary computer performs
routing by passing along the message to the next computer. Part of this
process involves analyzing a routing table to determine the best path.
Routing is often confused with bridging, which performs a similar function. The principal difference between the two is that bridging occurs at a lower level and is therefore more of a hardware function whereas routing occurs at a higher level where the software component is more important. And because routing occurs at a higher level, it can perform more complex analysis to determine the optimal path for the packet.
Routing is often confused with bridging, which performs a similar function. The principal difference between the two is that bridging occurs at a lower level and is therefore more of a hardware function whereas routing occurs at a higher level where the software component is more important. And because routing occurs at a higher level, it can perform more complex analysis to determine the optimal path for the packet.
Router
Routers are small physical devices that join multiple networks together. Technically, a router is a Layer 3 gateway device, meaning that it connects two or more networks and that the router operates at the network layer of the OSI model.
Home networks typically use a wireless or wired Internet Protocol (IP) router, IP being the most common OSI network layer protocol. An IP router such as a DSL or cable modem broadband router joins the home's local area network (LAN) to the wide-area network (WAN) of the Internet.
By maintaining configuration information in a piece of storage called the routing table, wired or wireless routers also have the ability to filter traffic, either incoming or outgoing, based on the IP addresses of senders and receivers. Some routers allow a network administrator to update the routing table from a Web browser interface. Broadband routers combine the functions of a router with those of a network switch and a firewall in a single unit.
Home networks typically use a wireless or wired Internet Protocol (IP) router, IP being the most common OSI network layer protocol. An IP router such as a DSL or cable modem broadband router joins the home's local area network (LAN) to the wide-area network (WAN) of the Internet.
By maintaining configuration information in a piece of storage called the routing table, wired or wireless routers also have the ability to filter traffic, either incoming or outgoing, based on the IP addresses of senders and receivers. Some routers allow a network administrator to update the routing table from a Web browser interface. Broadband routers combine the functions of a router with those of a network switch and a firewall in a single unit.
What is a Firewall ?
A firewall is a system designed to prevent unauthorized access to or from a private network. You can implement a firewall in either hardware or software form, or a combination of both. Firewalls prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet (i.e., the local network to which you are connected) must pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.
Note: In
protecting private information, a firewall is considered a first line of defence;
it cannot, however, be considered the only such line. Firewalls are generally
designed to protect network traffic and connections, and therefore do not
attempt to authenticate individual users when determining who can access a
particular computer or network.
Several types of firewalls exist:
- Packet filtering: The system examines each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible to IP spoofing.
- Circuit-level gateway implementation: This process applies security mechanisms when a TCP or UDP connection is established. Once the connection has been made, packets can flow between the hosts without further checking.
- Acting as a proxy server /Application Level: A proxy server is a type of gateway that hides the true network address of the computer(s) connecting through it. A proxy server connects to the Internet, makes the requests for pages, connections to servers, etc., and receives the data on behalf of the computer(s) behind it. The firewall capabilities lie in the fact that a proxy can be configured to allow only certain types of traffic to pass (e.g., HTTP files, or web pages). A proxy server has the potential drawback of slowing network performance, since it has to actively analyze and manipulate traffic passing through it.
- Web application firewall: A web application firewall is a hardware appliance, server plugin, or some other software filter that applies a set of rules to a HTTP conversation. Such rules are generally customized to the application so that many attacks can be identified and blocked.
In
practice, many firewalls use two or more of these techniques in concert.
In Windows 7, Vista, and XP, software
firewalls are built into the operating system. Earlier versions of Windows did
not have firewalls built in. Macintosh computers running Mac OS X 10.2 and
later are also equipped with a built-in firewall.
Third-party firewall packages also exist,
such as Zone Alarm, Norton Personal Firewall, Tiny, Black Ice Protection, and
McAfee Personal Firewall. Many of these offer free versions or trials of their
commercial versions.
Gateway
A network gateway is an internet working system capable of joining together two networks that use different base protocols. A network gateway can be implemented completely in software, completely in hardware, or as a combination of both. Depending on the types of protocols they support, network gateways can operate at any level of the OSI model.
Because a network gateway, by definition, appears at the edge of a network, related capabilities like firewalls tend to be integrated with it. On home networks, a broadband router typically serves as the network gateway although ordinary computers can also be configured to perform equivalent functions.
MPLS
Short for Multiprotocol Label Switching, MPLS is a process where data packets are given labels. When the data packets are transmitted over a network connection, instead of having to examine the packet contents to determine the network destination, the label contents can be examined and sent to its destination in a more efficient manner. This can improve data transmission speeds because there is no need to use a routing table to do a lookup on where the data packet is being routed to.
Due to the virtual paths between network nodes, MPLS is not dependent on an OSI model data link layer. It also virtually eliminates the necessity to use layer-2 networks for different types of network traffic. By including the MPLS header, containing one or more labels, to each data packet, networks gain a much needed improvement in data transmission efficiency, helping to decrease costs in the end.
Leased Line
Telephone line or data line that is rented by a private individual or company from a telephone company or data line provider. A leased line is always connected and does not require any special number in order to be connected. A great example of a common leased line is a T1 data line.
A service contract between a customer and provider is said to be a
leased line. Service provider agrees to provide a symmetric telecommunication
line connecting different locations whereby the consumer agrees to pay a
monthly rent. It does not have a telephone number unlike traditional PSTN
lines. Each side of the line is connected to the other. Leased lines can be
used for data, Internet, or telephone. Some connect two PBXs and some are ring
down services.
Leased lines are mostly used by businesses to
connect their distant offices. It is always active unlike dial-up connections.
A leased line is hired on a yearly basis. It may carry voice, data, or both.
The main benefits of leased lines are that they are private so the security
level is higher along with speed, reliability, and resilience
SPOOF
In general, the term spoof refers to hacking or deception that imitates another person, software program, hardware device, or computer, with the intentions of bypassing security measures. One of the most commonly known spoofing is IP spoofing.
IP spoofing:
A method of bypassing security measures on a network or a method of gaining access to a network by imitating a different IP address.
Some security systems have a method of helping to identifying a user by
his or her IP address or IP address range. If the attacker spoofs their
IP address to match this criteria it may help bypass security measures.
This technique is also used to deceive a web page, poll, or other
Internet contest into thinking the user is someone else allowing him or
her to get more hits or falsely increase a votes rank.
E-mail or address spoofing:
Process of
faking a senders e-mail address. This
form of spoofing is used to fool the recipient of the e-mail into
thinking someone else sent them the message. This is commonly used to
bypass spam filters or to trick the user into thinking the e-mail is safe when in reality it contains an attachment that is infected with a virus or spam.
- Getting bounce back e-mails from addresses I don't know.
Phone number spoofing:
It is possible for anyone to fake the number or
areacode they are calling from. This type
of spoofing is done by telemarkers to hide their true identity and by
hackers to gain access to unprotected phone voicemail messages.
Web page spoof:
A fake web page
or spoof on another commonly visited page. For example a malicious user
may create a spoof page of Microsoft's, eBay, PayPal or Google's home
page that looks identical but is hosted on a different server. These
pages are commonly used in phishing e-mails to extract information from the user such as usernames and passwords or to send malicious files to them.
Web page spoofing may also be done through IP
cloaking.
ACL
Access Control List, ACL is a listing containing one or more ACE that tells a computer operating system or other network device what rights users have to each item on a computer or network device. For example, an ACL may specify if a user or the users group have access to a file or folder on that computer or network.
Fiber-Optic
 Fiber-optic
cables are hollow cables that send data by pulses of light. Fiber
optics allows for a much faster data transmission because of the
capability of transmitting data at the speed of light. Most home
computer users will never get the opportunity to work with fiber-optic
cables because almost all home networks use other cables or wireless
connections to connect their computers together. Fiber-optic cables are
most often used in corporate networks or world-wide networks such as
Internet backbones because of
the capabilities of the cable.
In the picture to the right, is an example of fiber-optic cabling.
Fiber-optic
cables are hollow cables that send data by pulses of light. Fiber
optics allows for a much faster data transmission because of the
capability of transmitting data at the speed of light. Most home
computer users will never get the opportunity to work with fiber-optic
cables because almost all home networks use other cables or wireless
connections to connect their computers together. Fiber-optic cables are
most often used in corporate networks or world-wide networks such as
Internet backbones because of
the capabilities of the cable.
In the picture to the right, is an example of fiber-optic cabling.Caution: When handling and using fiber-optic cables or fiber-optic networking equipment, keep the below suggestions in mind.
- Keep the fiber connections and connectors capped when not in use to help prevent dust, dirt, or other substances from being on the connection of connector.
- Always keep the fiber connections and connectors clean.
- Do not allow the fiber cabling to bend more than the diameter of your fist. Bending the cable further could cause physical damage to the cable.
- Do not touch the tip of the actual fiber cabling, this could cut you.
- Never look down the fiber cabling when in use as light pulses are being used. To determine if the pulse is being sent, use a meter.
DOS
1. Short for Disk operating system, DOS is an acronym often used to describe MS-DOS.
2. Short for Disk operating system, DOS
refers to any operating system that runs from a disk drive.
Today, all operating systems can be considered disk operating systems.
3. Short for Denial of Service, a DOS attack is a form of attacking another computer or company by sending millions or more requests every second causing the network to slow down, cause errors or shut down. Because it is difficult for a single individual to generate
enough traffic for a DoS attack to be successful, these attacks are usually
run from multiple computers infected by worms
that have created zombie computers to all run
at the same time to generate a DDoS attack.
Standards
IANA:
Short for Internet Assigned Numbers Authority, IANA is managed by ICANN (Internet Corporation for Assigned Names and Numbers), with oversight from the United States Department of Commerce. IANA manages IP addressing, the Domain Name System root zone, protocol assignments, and more.ICANN:
Short for Internet Corporation for Assigned Names and Numbers, ICANN is responsible for Internet Protocol (IP) address space allocation, protocol identifier assignment, and generic and country code Top-Level Domain names.ICA:
1. Short for Independent Computing Architecture, ICA is a thin protocol developed by Citrix
for separating screen updates and user input processing from the rest
of the application's logic. This enables for remote accessibility with
less bandwidth consumption as only the screen updates,
mouse movements, and
keyboards are sent over the session.
- Computer network and network card help and support
2. Short for Integrated Communications Adapter, ICA is an adapter used with the IBM 9370 series and 4300 series mainframes that eliminate the need for a separate communications controller.
IEEE 802 standards
The standard that was set by IEEE for networking, specifically through local-area networking or LANs. Below is a listing of just some of the 802 standards currently referenced in the Computer Hope database.
802.2
802.3
802.3ab
802.3ae
802.3u
802.3z
802.11a
802.11b
802.11g
802.12
802.16
802.3
802.3ab
802.3ae
802.3u
802.3z
802.11a
802.11b
802.11g
802.12
802.16
LLC:
1. Short for Logical Link Control, LLC
is the upper portion of the data link layer defined in IEEE 802.2. The
LLC provides the user an interface to the data link layer
of the OSI model and provides a uniform interface for users of the
data link
service. Today, 802.2 is considered inactive.
- Computer network and network card help and support
2. Short for Limited Liability Corporation,
a LLC is a corporation started by small businesses or business
owners that allows a business to be a corporation without the high taxes
and allows the owners to not be held responsible, only the company.
Ethernet:
Originally known as Alto Aloha Network, Ethernet is a widely used local-area network (LAN) protocol originally created by Xerox PARC in 1973 by Robert Metcalfe and others (U.S. Patent # 4,063,220). Being the first network to provide Carrier Sense Multiple Access / Collision Detection (CSMA/CD), Ethernet is a fast and reliable network solution that is still widely used today. Below is a listing of different standards of Ethernet and additional information about each of them.
Ethernet II / DIX / 802.3:
Ethernet II is a revised version of Ethernet rewritten by with Digital
Equipment Corp, Intel, and Xerox. Ethernet II, also known as DIX, (Digital, Intel, and Xerox) and 802.3.
Fast Ethernet / 100BASE-T / 802.3u:
Fast
Ethernet is also referred to as 100BASE-T or 802.3u and is a
communications protocol that enables computers on a local-area network
to share information with one another at rates of 100 million bits per
second instead of the standard 10 million BPS. Fast Ethernet works over Category 5 twisted-pair wiring.
There are two available 100BASE-T standards. The first standard known as 100BASE-T utilizes CSMA/CD. The second standard, known as 100VG-AnyLAN or 802.12, is similar to the other standard; however, it utilizes a different Ethernet frame to send its data.
100BASE-T is available in three different cable technologies:
- 100BASE-T4 = Utilizes four pairs of telephone-grade twisted-pair wire and is used for networks that need a low-quality twisted-pair on a 100-Mbps Ethernet.
- 100BASE-TX = Developed by ANSI 100BASE-TX is also known as 100BASE-X, 100BASE-TX uses two wire data grade twisted-pair wire
- 100BASE-FX = Developed by ANSI, 100BASE-FX utilizes 2 stands of fiber cable.
Ethernet SNAP:
Ethernet SNAP is short for Ethernet SubNetwork Access Protocol and is
an Ethernet protocol that enabled old and new protocols to be encapsulated in a type 1 LLC.
Gigabit Ethernet / 1000BASE-T / 802.3z / 802.ab:
Gigabit Ethernet is also known as 1000BASE-T or 802.3z / 802.3ab is a later Ethernet technology that utilizes all four copper wires in a Category 5 (Cat 5 & Cat 5e) capable of transferring 1 Gbps.
10 Gigabit Ethernet / 802.3ae:
10 Gigabit Ethernet is also known as 802.3ae is a new standard that supports 10.000 Gb/s.
1000BASE-CX:
A copper cable gigabit Ethernet standard that is no longer used. This standard has been replaced by 1000BASE-T.
1000BASE-LX:
A fiber optic gigabit Ethernet standard that operates over single-mode fiber.
1000BASE-SX:
A fiber optic gigabit Ethernet standard that operates over multi-mode
fiber with typical distances of up to 550 meters (1804 feet)
Ethernet adapter:
An Ethernet adapter or Ethernet controller
is a term used to describe an Ethernet network card used to connect a
desktop computer to a network. If you are looking for network adapter
drivers, you can find them through our network drivers page.
IEEE 802.11:
The IEEE
802.11 is a standard introduced by IEEE
in June 1997 used for wireless Ethernet networks. Below is a listing of each of
the wireless IEEE standards currently available. Home users should only be
concerned about 802.11a, 802.11b, or 802.11g for their home wireless network.
Standard
|
Description
|
IEEE
802.11
|
The
initial release of the standard capable of transmissions of 1 to 2 Mbps
and operates in the 2.4 GHz band.
|
IEEE
802.11a
|
Capable
of transmissions of up to 54 Mbps
and operates in the 5 GHz band.
|
IEEE
802.11b
|
Introduced
in 1999, 802.11b is capable of transmissions of up
to 11 Mbps and operates in the 2.4 GHz
band.
|
IEEE
802.11c
|
Defines
wireless bridge operations
|
IEEE
802.11d
|
Defines
standards for companies developing wireless products in different countries.
|
IEEE
802.11e
|
Defines
enhancements to the 802.11 MAC
for QoS.
|
IEEE
802.11f
|
Defines
Inter Access Point Protocol (IAPP)
|
IEEE
802.11g
|
Capable
of transmissions of up to 20 Mbps
and operates in the 2.4, 3.6 and 5 GHz
bands.
|
IEEE
802.11i
|
Improved
encryption (WPA).
|
IEEE
802.11j
|
802.11
extension used in Japan.
|
IEEE
802.11n
|
Operates
using the 2.4GHz and 5GHz bandwidths. It utilizes multiple-input,
multiple-output (MIMO) antennas to improve data transfer speeds.
|
WiMAX:
Alternatively referred to as IEEE 802.16, WiMAX is short for Worldwide Interoperability for Microwave Access and is a wireless microwave technology used in MAN that provides connections up to 75Mbs as far away as 30 miles providing 30 to 40 megabit/sec data transfer speeds. An update in 2011 allowed WiMAX to provide up to a 1 gigabit/sec transfer speed. In a basic sense, WiMAX is similar to WiFi technology, except that it can provide much higher data transfer rates, causing some people to call it "WiFi on steroids". It is also based on the IEEE 802.16 standard, whereas WiFi is based on the IEEE 802.11 standard.Now referred to as Fixed WiMAX, the standard was originally published in 2001. WiMAX can provide internet access across cities and even countries, using various devices for connectivity. For those customers that are unable to get broadband cable or DSL access, WiMAX may provide an alternative option for them for getting Internet access. It's also possible to use WiMAX for VoIP phone calls and IPTV services.
Subscribe to:
Posts (Atom)